To set up an EAP 802.1x user policy-based authorization.
Before this setup
To start the setup. You should follow this article to understand the internet interface (bridge/tunnel mode) first.
This article will show how to set up a user authorization with WPA2 Enterprise
https://peterliu.top/index.php/archives/1168
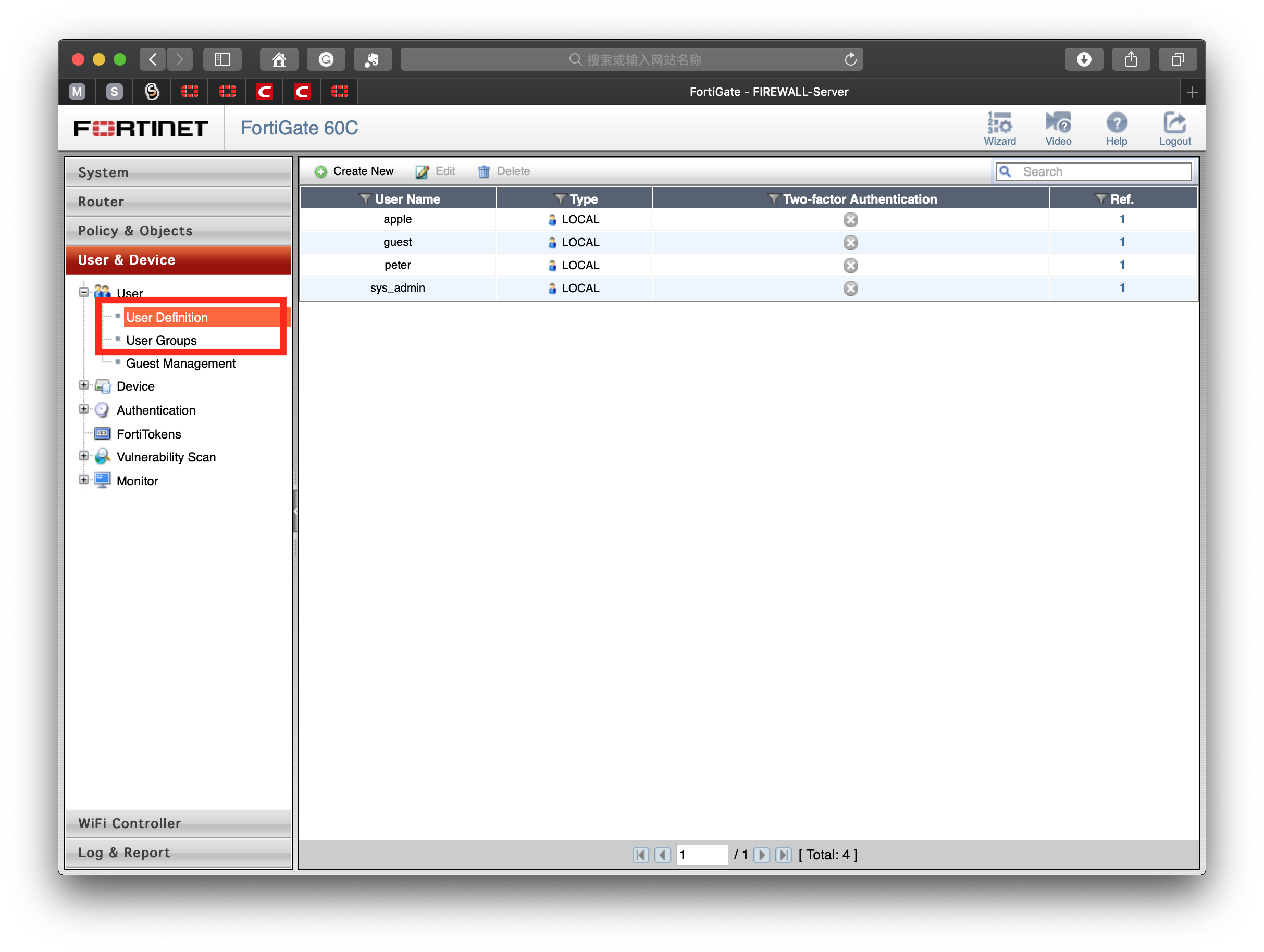
Add a local user and local group
User&Device> User Definition > Create New > Local > Username/Password
User&Device> User Group > Create New > Firewall > Add User
Create the WiFi network
Login into your FortiGate that you wish to set up to be a controller.
Go To System > CLI
If you have not set up a wifi-certificate for system authorization, Apple devices such as iPhone, iPad, iPod, Mac cannot connect to the WiFi successfully.
config system global set wifi-certificate "Fortinet_CA" set wifi-ca-certificate "Fortinet_CA"
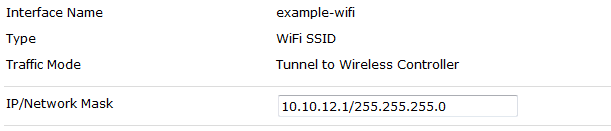
Go To WiFi Controller > SSID > Create New
When you are using the enterprise authentication, it is available to use tunnel mode or bridge.
If you don’t understand bridge and tunnel mode read the article in “begin this step” section.
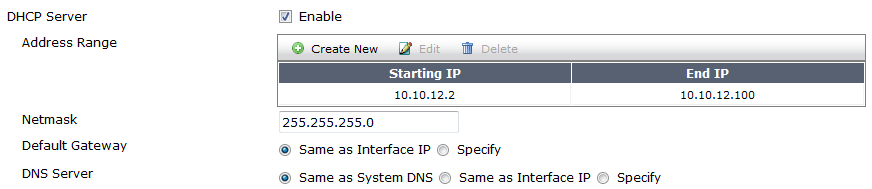
Enable DHCP for clients.
Change the security mode to WPA2 Enterprise.
Select the local authentication, and choose the authentication group.

Create the Internet access security policy
Go to Policy & Objects > Policy > IPv4.
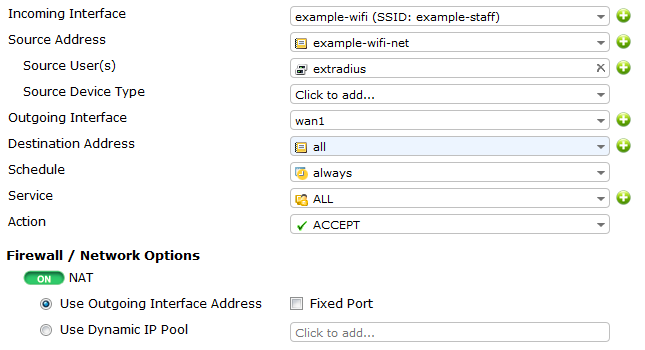
Set up incoming WiFi traffic to assess outgoing internet to access the internet.
Connect and authorize the FortiAP
Read this article: https://peterliu.top/?p=1168&preview=true
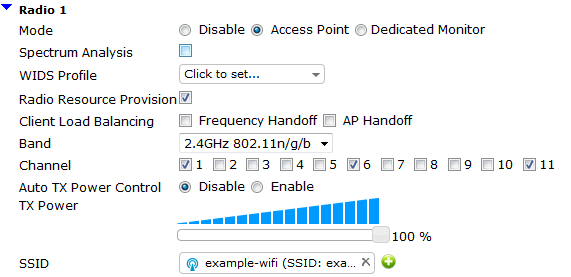
Result:
When you connect to the network SSID. The system will require your username and password.
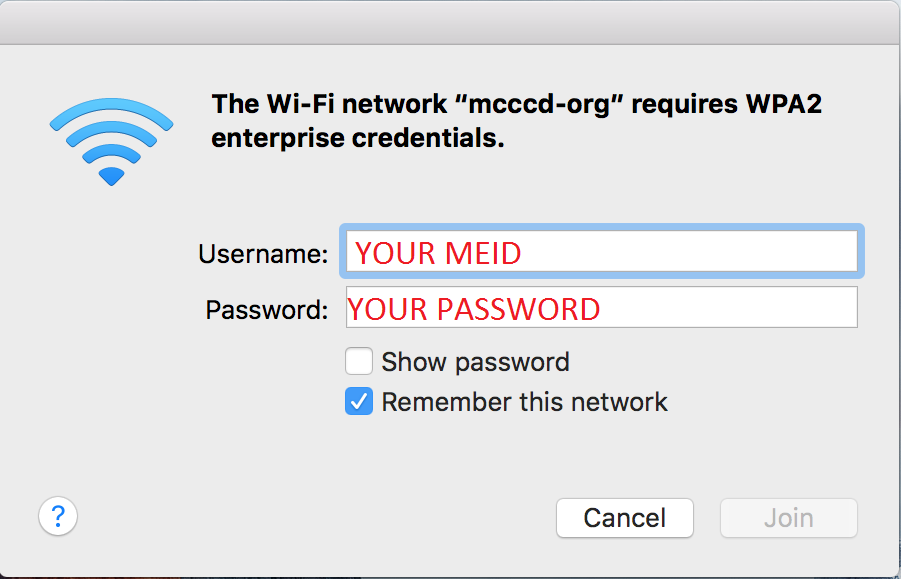
REF<WPA2 WiFi access control >: https://cookbook.fortinet.com/wp2a-wifi-access-control/
REF<Fortigate/FortiAP: device based authentication using certificates>: https://forum.fortinet.com/tm.aspx?m=110985