For set up multi VPN tunnel for any VPN server, you should understand how VPN service work. Each VPN have two tunnel it calls “phase1” and “phase2”. While you connect VPN client to server phase1 will auth user information and password fit the record of the server. If yes, phase2 will send the packet from server to client. Which means VPN had connected successfully.
Why do Multiple VPN Fail?
When VPN tunnel communicates with the client, it will block other data send from another auth client. That means phase1 can only use for auth one IPSEC VPN. We either use policy control to separate different user group to fit different permission or set a unique peer id to solve this problem.
How to Fix and Set Up Multiple VPN.
I will take policy control to be the solution because it is easier that the other one.
Set up a VPN tunnel.
For FortiOS 5, you can use a template that already set in firewall to create a iOS/Android IPSec.
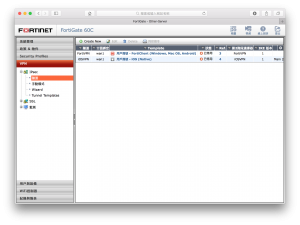 This area located at right sidebar VPN tab. If there are no this option. Check features in System Management > Setting > Feature, make sure VPN feature are opened.
This area located at right sidebar VPN tab. If there are no this option. Check features in System Management > Setting > Feature, make sure VPN feature are opened.
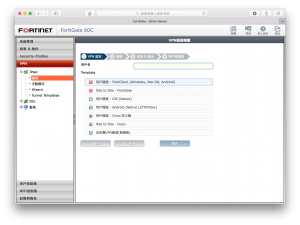 Randomly gave a name for this VPN and set outbound and inbound to WAN1. Also gave a IP range for VPN Client.
Randomly gave a name for this VPN and set outbound and inbound to WAN1. Also gave a IP range for VPN Client.
 After that, click to the VPN tunnel you create and set XAUTH to inherit form policy group.
After that, click to the VPN tunnel you create and set XAUTH to inherit form policy group.
Set up a VPN policy group.
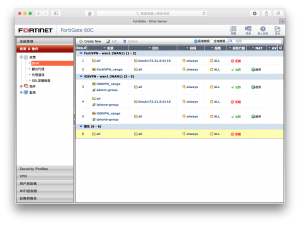 Go to right bar, you will see “Policy and Object” and find the VPN policy line.
Go to right bar, you will see “Policy and Object” and find the VPN policy line.
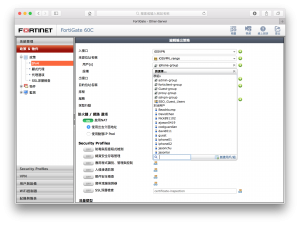 Next Set a group to assign different policy and permission
Next Set a group to assign different policy and permission
Finally, you can config different group and policy to fit different permission you want.