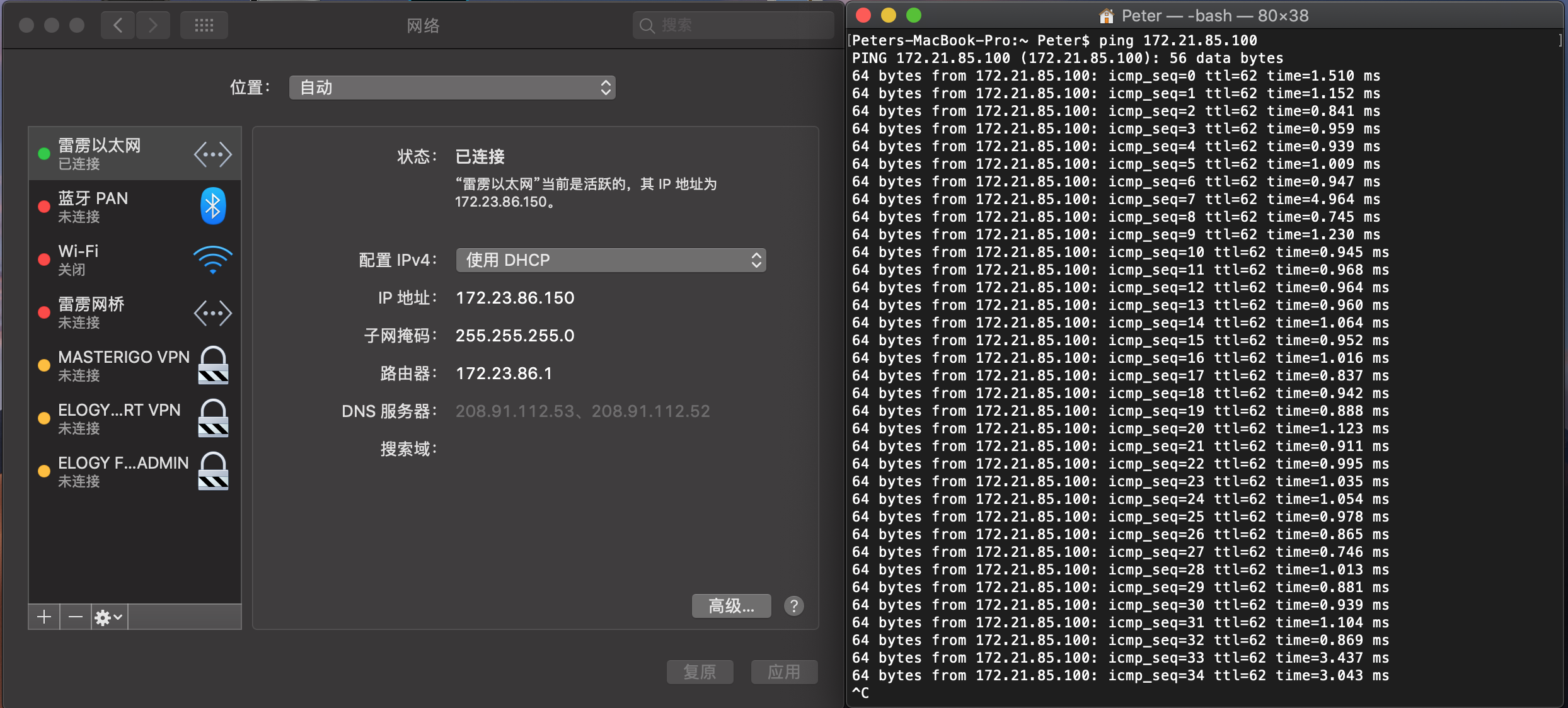
To Learn How to Setup Site to Site VPN in Fortigate (FortiOS 5.0-5.2)
Some enterprise separate VPN server with firewall or other server to deploy a high load and reliable system. When I configured Site to Site VPN by connecting 172.23.86.1 and 172.16.20.1 together. I like to enable the session from 172.23.86.1 to access WAN1(172.21.85.30) of my VPN Server. 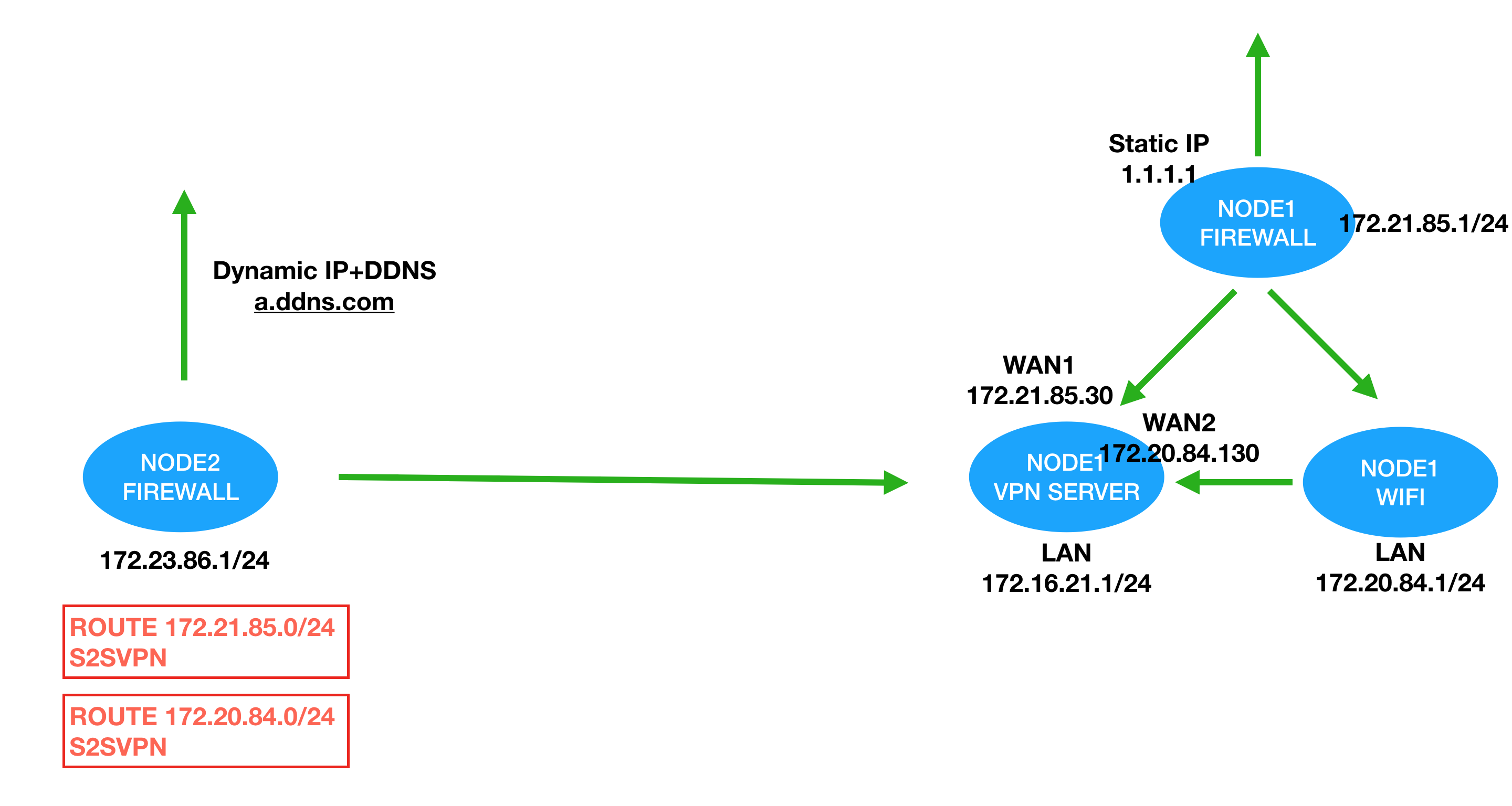 This article teach you how to create a multi subnet site to site VPN with only single access (172.23.86.1 allow to access 172.21.85.1, but not 172.21.85.1 to access 172.23.86.1)
This article teach you how to create a multi subnet site to site VPN with only single access (172.23.86.1 allow to access 172.21.85.1, but not 172.21.85.1 to access 172.23.86.1)
First, make sure you had setup a policy base site to site VPN phase.
[Fortigate] Setup a Site to Site VPN with DDNS or Static IP (FortiOS 5.0-5.2)
Understand How Does Policy Work.
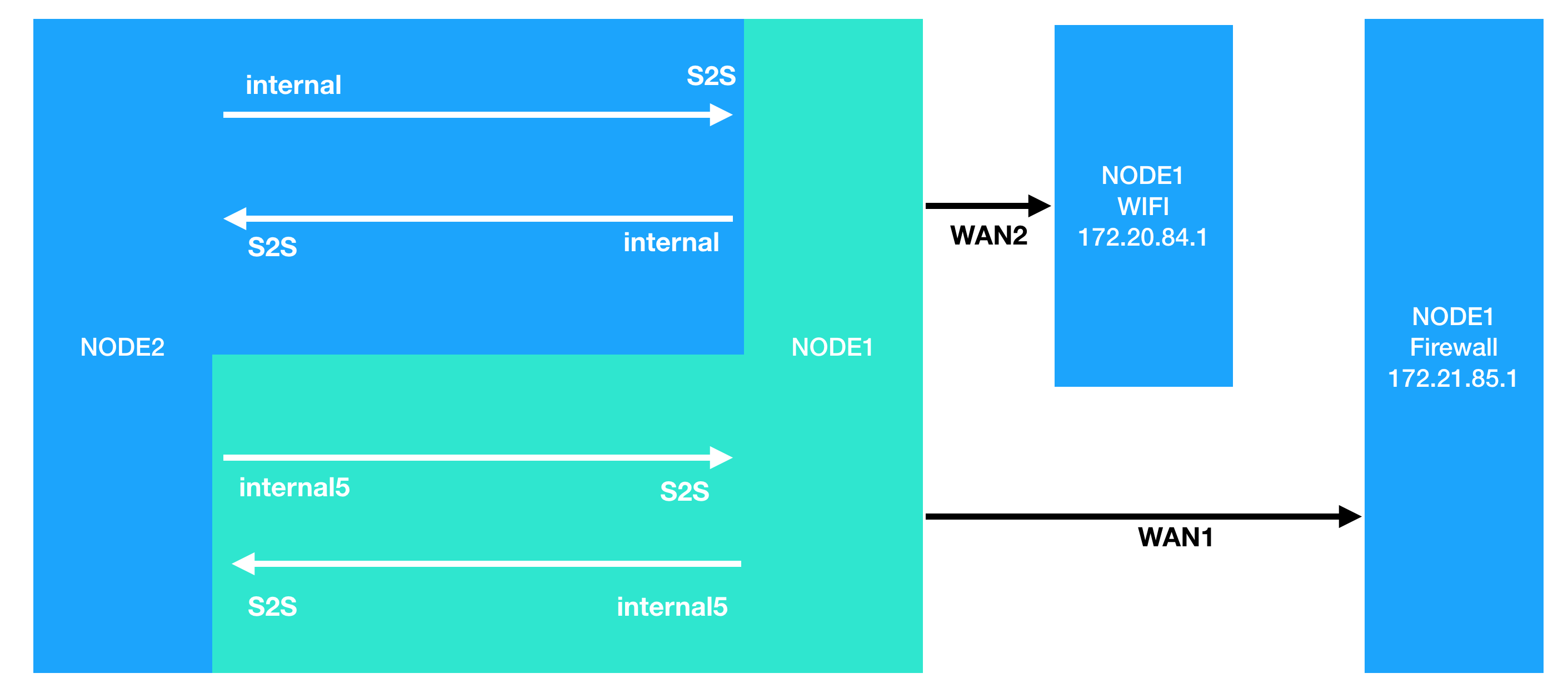 There are two policy per node to allow remote to access local (node2 to node1), local to access remote (node1 to node2). According to the graphic, node1 and node2 just allow each other to connect to LAN interface.
There are two policy per node to allow remote to access local (node2 to node1), local to access remote (node1 to node2). According to the graphic, node1 and node2 just allow each other to connect to LAN interface.
Adding Route to Navigate Traffic.
We should tell node2 to send traffic of 172.21.85.0/24 via S2SVPN tunnel to node1 Setup a route of 172.21.85.0/24 using interface S2SVPN 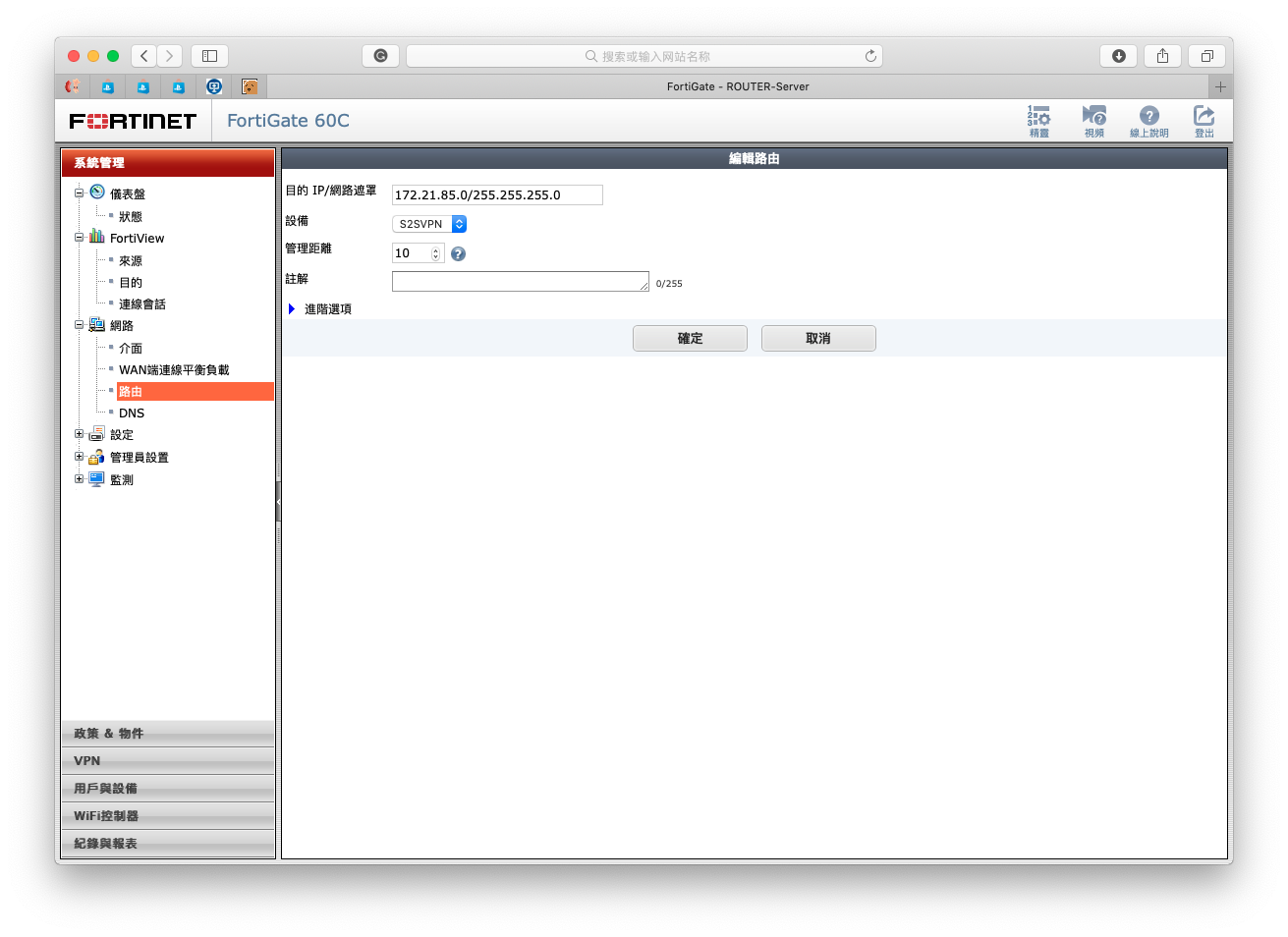 Route: To tell traffic which tunnel should go.
Route: To tell traffic which tunnel should go. 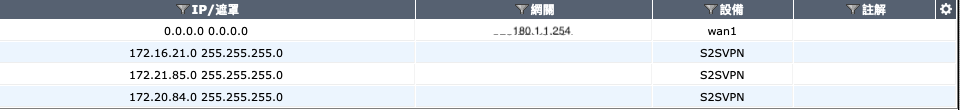 For example, 0.0.0.0 (All the traffic) to Gateway 180.1.1.254 Tunnel WAN1 172.16.21.0/24 to Tunnel S2SVPN 172.23.85.0/24 to Tunnel S2SVPN 172.21.85.0/24 to Tunnel S2SVPN
For example, 0.0.0.0 (All the traffic) to Gateway 180.1.1.254 Tunnel WAN1 172.16.21.0/24 to Tunnel S2SVPN 172.23.85.0/24 to Tunnel S2SVPN 172.21.85.0/24 to Tunnel S2SVPN
Adding Policy in Node2 (Branch Remote Office).
We had already set S2SVPN to Local Subnet and Local Subnet to S2SVPN. But this policy only sent 172.16.21.0/24 (node1 internal). Now we should add to sent 172.21.85.0/24 in S2SVPN
You can add the policy with address object either an address type in.
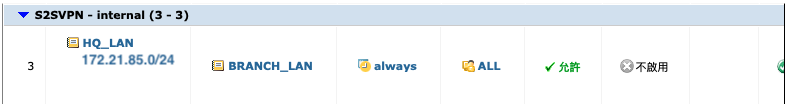
From S2SVPN “HQ_LAN1” to Internal “Branch_LAN1”: remote to access Node2 .(without NAT)
From S2SVPN “172.21.85.0/24” to Internal “Branch_LAN1”: firewall to access Node2 .(without NAT) From Internal “Branch_LAN1” to S2SVPN “HQ_LAN1” : local to access Node1.(without NAT)
From Internal “Branch_LAN1” to S2SVPN “”172.21.85.0/24″” : local to access Node1 Firewall.(without NAT)

Adding Policy in Node1 (HQ Local Office).
We had already set S2SVPN to Local Subnet and Local Subnet to S2SVPN. But this policy only sent 172.16.21.0/24 (node1 internal). Now we should add to sent traffic of S2SVPN to WAN1 You can add the policy with address object either an address type in.
From S2SVPN “Branch_LAN1” to Internal “HQ_LAN1”: remote to access Node1 .(without NAT)
From Internal “HQ_LAN1” to S2SVPN “Branch_LAN1” : local to access Node2.(without NAT)
From S2SVPN “Branch_LAN1” to WAN1 “172.21.85.0/24”: remote to access 172.21.85.0(Firewall). (WITH NAT!!!) ![]()